A VPN (virtual private network) is an encrypted network connection. The term “virtual” denotes a collection of software controls and tunneling. The VPN forms the end-to-end connection, rather than using dedicated lines and hardware. Also, “tunneling” means transmitting the encrypted data packet within another packet.
So, a VPN shows the user’s IP (internet provider) address as the VPN server the user connects to. That server is typically outside the geographic area of the VPN user. The connection is encrypted and totally secure. As the VPN routes the user to the desired destination site or network, the data to and from the user and the site/network is encrypted.
When the user’s connection plugs into the public web, the data stays secure, especially when the telltale “S” follows the “HTTP” address designation. However, using a VPN to visit insecure websites still makes the user hard to trace, because the data appears to originate from a location other than the users.
What a Virtual Private Network Does
In the simplest words – it provides an extra element of deception for individuals and businesses.
What a VPN does best is:

Source: pcmag.com
Masks (hides) the user’s online activity
A Virtual Private Network provider like this website with a “no-logs” policy” collects absolutely no information on the user’s web activity. ISPs have begun to follow the example of Google and Facebook’s data-mining practices. They target for targeted users for advertising analytics collection for sale to marketers. It provides a block and stops sign for users who don’t want to be tracked, even anonymously.
Safeguards against Internet censorship
Some governments block their citizens from accessing what they consider subversive websites. It bypasses censorship through location masking.
Defeats geo-blocking
Geo-blocking is a measure that detects the user’s geographical location in order to block access to content normally restricted to local users. Some vendors, for example, have different price structures for affluent geographical areas. They use unfair pricing tactics to geo-block users seeking lower prices.
Provides deception while using unprotected public Wi-Fi.
Public Wi-Fi “hot spots” are spreading worldwide. Logging into a public Wi-Fi spot without the protection of a Virtual Private Network is an open invitation to a man-in-the-middle (MITM) attack.
How It Keeps You Safe from MITM Attacks
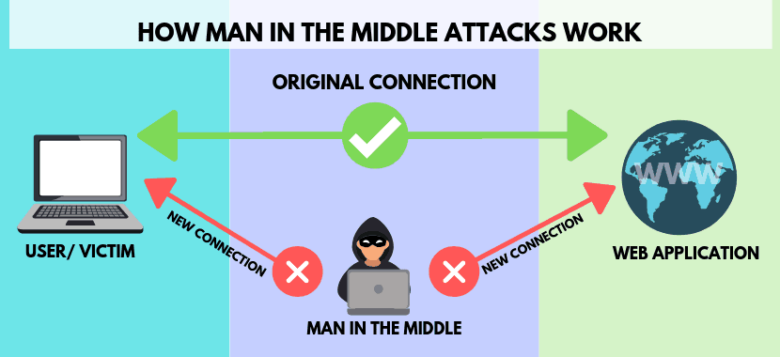
Source: phoenixnap.com
What is MITM?
A man-in-the-middle attack occurs when a hacker hijacks an insecure connection. The hacker gets in the middle of a two-party transaction on the web, either or both parties and gains access to the information they are transacting.
To carry out the MITM attack, hijackers use the following strategies:
- detecting and accessing unsecured networks with a “web pineapple” device
- “sniffing out” online activity and intercepting the data going to and from the victim
- using a spoofed website or fake web application and sending a user to a hijacked web application controlled by the attacker
- stealing session cookies and unencrypted login information, even when the site is secure.
How a Virtual Private Network Protects Against MITM Attacks
Obviously, the best safeguard against attacks is to never connect to insecure public Wi-Fi routers. However, there are alternatives that provide a more secure way to get on the web while traveling:
- For users who have lots of mobile data, using a smartphone as a Wi-Fi hotspot for a laptop Internet connection is a safe method. Known as Wi-Fi tethering, this method can be expensive, because it taps into the user’s mobile data charges.
- Using a personal portable Wi-Fi router can be a safe and secure alternative to logging into someone else’s slow, insecure system. For an upfront investment (around $100 or less), a traveler can log on anywhere in the world.
Nevertheless, when a public Wi-Fi is the best and only option for the traveler, using a virtual private network (Virtual Private Network and employing sensible security practices will shield the user against intruders.
A Word of Caution
Virtual Private Networks have encryption protocols with built-in security features, but they do not provide full protection against virus injection against phishing or if the user clicks on links in unsecured web sites. Always rely on built-in anti-virus programs and web malware detectors. Think of a VPN as an invisible mobile shield. It hides the user’s IP address and spoofs the user’s location, and is an added safeguard. A VPN is no substitute for strong password strategies, file encryption, and other sensible security practices. Those practices consist of avoiding insecure websites and avoiding social engineering scams.
More Virtual Private Network Benefits

Source: pcmag.com
It bypass ISP bandwidth throttling
The user can access games available only to local users. The user’s true location is hidden and displays the user’s location as where the game is available. The Virtual Private Network also blocks interference by rival players.
Enjoy Netflix and other streaming services
With a strong service, you can access streaming services like Netflix from outside the area. Netflix streaming is frequently restricted by copyright agreements. For example, US users can be blocked from a popular UK series. Sign in through a UK server and unlock vast amounts of content without having to download entertainment from dangerous virus prone websites.
Sports fans can get full access to geo-blocked events
Use a strong Virtual Private Network to view favorite locally blocked sports channels. While watching streamed live events from home, it allows the viewer to bypass ISP throttling, which rations bandwidth to local users. Also, it exempts viewers from bandwidth throttling during primetime viewing hours.
A Virtual Private Network gives Bitcoin mining and trading an extra level of security

Source: weforum.org
It provides even greater security in the already encrypted cryptocurrency transactions—i.e., bitcoin trading and mining. While blockchain technology provides a secure ledger to safeguard bitcoin owners, access keys to individual user accounts have been stolen through phishing and bot injections.
Once the bitcoin has been stolen or “side jacked,” it cannot be recovered. A Virtual Private Network is another level of insurance against Bitcoin theft. It masks the user’s online activity and adds another layer of anonymity and hides the owner’s connection.
How to Set It Up
You set up a Virtual Private Network by logging into a free or premium service provider. Installation instructions vary, depending on the computer operating system, and most services are user friendly and easy to follow.
Free Vs. Premium
A free service is a stripped-down version of a premium product. The free one remains free by loading ads into the user’s browser and comes with some security and privacy weaknesses. A good rule of thumb then is to avoid free Virtual Private Network services because:
Free Ones track your online activity.
Studies at Virtual Private Network Mentor showed that over 70% of free ones have embedded trackers. Those trackers collect data on the user’s online activity and destinations and target the user with online adds. Free VPN services also sell collected data to marketers.
Free ones slow down the user’s internet speed.

Source: wordpower-software.com
Free Virtual Private Network users will often be bumped by to the back of the queue by paying customers in sharing bandwidth. Also, since free ones are supported by internet advertisers, they generate annoying ad popups. Those jumping popups can slow browser performance and provide a distracting user experience.
Free Virtual Private Networks open the user to secondary attacks.
They are more prone to expose the user to spyware than their premium counterparts. Most of the malware in the free ones come through hidden viruses and bots embedded advertising links and images. SecureLink mentions that while VPNs can handle internal access, using a basic VPN connection for third parties can expose a business network to more vulnerabilities, like hackers exploiting third-party connections or shared passwords. Although many businesses still use VPNs for all remote access, it’s important that all organizations realize a VPN’s limited capabilities and start looking for alternatives to VPN for remote access, especially when dealing with the specific unique access needs for different types of users.
Note: One Virtual Private Network provider freely admitted selling the user’s device processing power to paying customers. That same provider endangered its free customers by exposing them to a botnet network attack by cyber-criminals.
For just a few dollars per month a premium service can provide the following benefits:
- a guaranteed “no-logs” policy–The user is never tracked online and the service maintains no connection or activity logs for any user.
- best-in-class and secure connections with top-grade 256-bit encryption
- prevention of data leakage with a “kill switch” that closes the user’s connection if the VPN server goes down
- best and most effective means to bypass geo-blocking
- Attractive extras. For example, Clean Web™, a web app included with the Surfshark premium Virtual Private Network, blocks ads, trackers, malware and phishing attempts.
Summary and Conclusions
Source: zdnet.com
A Virtual Private Network provides an encrypted network connection to hide the user’s address and mask login information. A premium VPN protects the user’s privacy with “no-logs” policy. The VPN provider cannot collect information on the user’s web activity. A VPN also bypasses geo-blocking and provides protection when using public Wi-Fi. That protection thwarts man-in-the-middle intrusions and keeps the user’s activity hidden.
VPN’s, however, are not malware or virus hunters. They are an additional mobile shield and another level of insurance, which should be used in connection with other commonsense strategies.
Log into a premium VPN service and enjoy additional benefits like bypassing bandwidth throttling and enjoying unrestricted access to overseas streaming services and sports. A VPN is also another level of security for Bitcoin transactions.
Set up a VPN by logging into a free or premium service. Use a premium, low-cost service like Surfshark and enjoy a full range of security and better performance.




